

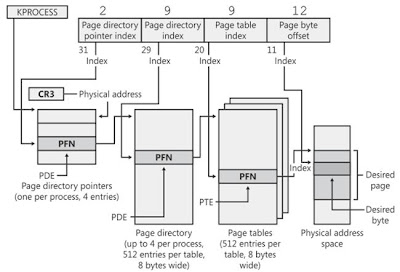
Windows Memory Management in PAE mode
Memory Dumping
•Dd.exe is a tiny tool from George M. Garner Jr.
Simple file format, file offset equals the address in physical memory
•Crash dump is supported by Microsoft Windows 2000/XP/Vista as a system feature.
It has its own format. Some pages are missing . Microsoft has kernel debugger to analysis it.
Why Search PD?
•Some useful structures are always fixed at the virtual memory addresses.
•Once the PD is found, the whole memory space for the process is exposed to investigator.
Current Method on PD Searching
•Andreas Schuster
The 4G memory space in Windows is split into two halves. The lower 2GB of virtual memory are available for the users, while the upper 2GB are reserved for the kernel. The kernel always maps some of the upper 2GB address to system kernel files, which only remains one copy in the memory. This means if we try to translate the upper 2GB virtual memory into physical addresses, many of them will converge into the same physical addresses. Most of these memory pages will look the same across all the processes.
•Joe Stewart
The method by Joe Stewart is much more efficient than the above one. Joe Stewart does not compare each page with the upper half. Instead, he makes use of the self-reference property of PD. We have introduced this property above. With the help of the special property, all we have to do is to take a look at the content in the entry of offset 0xC00 of each page, if the content equates to the physical address of the current page, we believe it is a page directory.
The method by Joe Stewart is much more efficient than the above one. Joe Stewart does not compare each page with the upper half. Instead, he makes use of the self-reference property of PD. We have introduced this property above. With the help of the special property, all we have to do is to take a look at the content in the entry of offset 0xC00 of each page, if the content equates to the physical address of the current page, we believe it is a page directory.

Constraints
•Neither of them handles Windows XP in PAE mode right now.
Our Method to Search PD in PAE


•The page that CR3 register points to plays 4 roles in one scene. First, it is the page that contains the page directory pointers; second, it is the last page directory of the 4 page directories; third, it acts as a page table; fourth, it is also a data page that can be visited by virtual address of 0xC0603000.
•The way to check a page whether it contains the page directory pointers is easy. The fourth entry must contain the physical address of the page.
Testing
•We used KUSER_SHARED_DATA to test whether the page directory pointers are right or not. To each process found, we used the PD to translate the virtual address 0x7FFE0000 and 0xFFDF0000. If all of the processes come out with the same physical address there is no false positive.
•As far as we can see, all the found processes come out with the same physical address: 0x41000.
•Also we print out some information contained in PEB to verify the page directory pointers.
Discussion
•During the analysis of dump file, we found that many processes have duplicated 1 or more of the page that contains the page directory pointers. Why does the operation system allocate another page rather than share the same page of PD and PT? This could be an interesting question. I guess the reason may lie on the flags in the each entry. Because different part of program have different right on the same page. The kernel may want to copy the page and set different flags. As our observation, the duplicated pages have same physical address but different flags.
No comments:
Post a Comment